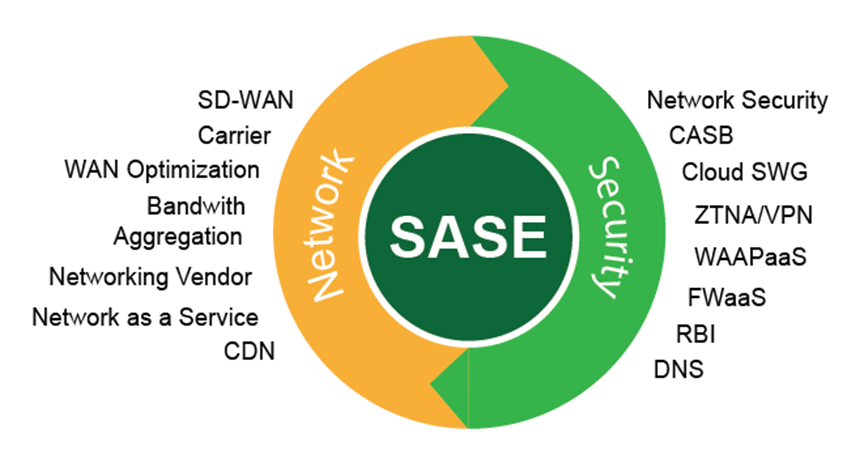
A more granular examination of the Secure Access Service Edge market uncovers several profound insights that go beyond the surface-level trends and reveal the true nature of this architectural shift. One of the most critical Secure Access Service Edge Market Insights is the understanding that SASE is not a single product that can be purchased and deployed, but rather an architectural journey that organizations undertake over time. Very few enterprises will, or should, attempt a "rip and replace" of their entire legacy infrastructure in one go. Instead, successful SASE adoption is almost always a phased process that begins by targeting a specific, high-priority pain point. For many, this journey starts with replacing their aging and insecure VPN infrastructure with a modern Zero Trust Network Access (ZTNA) solution to provide better security and user experience for remote workers. For others, the initial step might be deploying a Secure Web Gateway (SWG) and Cloud Access Security Broker (CASB) to gain visibility and control over cloud application usage. This insight is crucial because it highlights the importance of vendors offering a modular and flexible platform that allows customers to start small, realize immediate value, and then gradually expand their adoption to encompass the full suite of SASE capabilities at a pace that makes sense for their business.
A second, and perhaps the most fundamental, insight is that the Zero Trust security model is the philosophical and technical heart of the SASE framework. SASE is, in effect, the most practical and comprehensive way to implement a Zero Trust strategy across a distributed enterprise. While "Zero Trust" has become a popular marketing buzzword, its core principles are very specific: never trust, always verify; enforce least-privilege access; and assume breach. A true SASE architecture is built from the ground up to enforce these principles for every single connection request. It continuously authenticates and authorizes users based on their identity and device posture, it grants access only to the specific application or data resource requested (not the entire network), and it inspects all traffic for threats. The insight here is that any organization that is serious about moving beyond the rhetoric and actually operationalizing a Zero Trust security posture will inevitably find itself on a path to a SASE architecture, as it provides the necessary converged infrastructure to apply these principles consistently and at scale to all users, on all devices, accessing applications anywhere.
A third, powerful insight relates to the significant organizational and cultural impact that SASE adoption has within an IT department. For decades, enterprise IT has been characterized by deep silos, with the networking team and the security team operating as separate fiefdoms with their own distinct tools, budgets, and priorities. The networking team was primarily concerned with performance and uptime, while the security team was focused on risk mitigation and policy enforcement. The SASE framework, by its very nature as a convergence of networking and security into a single, cloud-delivered service, fundamentally breaks down these silos. Implementing and managing a SASE platform requires networking and security professionals to work together more closely than ever before, using a shared console and a unified policy engine. This technological convergence is forcing an organizational convergence, leading to the creation of new, integrated teams (sometimes called "Secure Access" or "Edge" teams) and fostering a more collaborative culture. This insight reveals that the impact of SASE is not just technological; it is also a catalyst for profound and positive organizational change.